As cybersecurity threats to controllers inside a vehicle increase, automakers(OEM) are specifying their requirements for cybersecurity function application.
To raise the cybersecurity level of the controller, application of HSM cybersecurity solution is mandatory, and stability, performance, cost, after service ease shall all be
considered for selecting the HSM cybersecurity solution.
how and what solutions should we apply?
-
OEMs ask for cybersecurity solution but I don’t know what to do.
-
Our current chipset requires HSM, and replacing them to implement cybersecurity is costly and time-consuming.
-
The cybersecurity solution cost is a burden, and engineering support is slow.
-
Solutions provided by semiconductor companies are difficult to meet OEM security requirements.
40+ different controllers.
-

- FESCARO developed HSM solution
-
- A-SPICE (Automotive SW dev. process & Quality Evaluation) LV2 certified
- US government(NIST)’s crypto algorithm related FIPS 140-2 certified
- Cryptographic library (FAST™ CLIB) implemented by crypto algorithm
- Compatible to various global automotive semiconductors
(8 Manufacturers, approx. 50 models & continuous support for new chips) - Immediate response is available if new request & update after production is required
-

- Meet OEM security requirements based on the international cybersecurity engineering standard (ISO/SAE 21434)
-
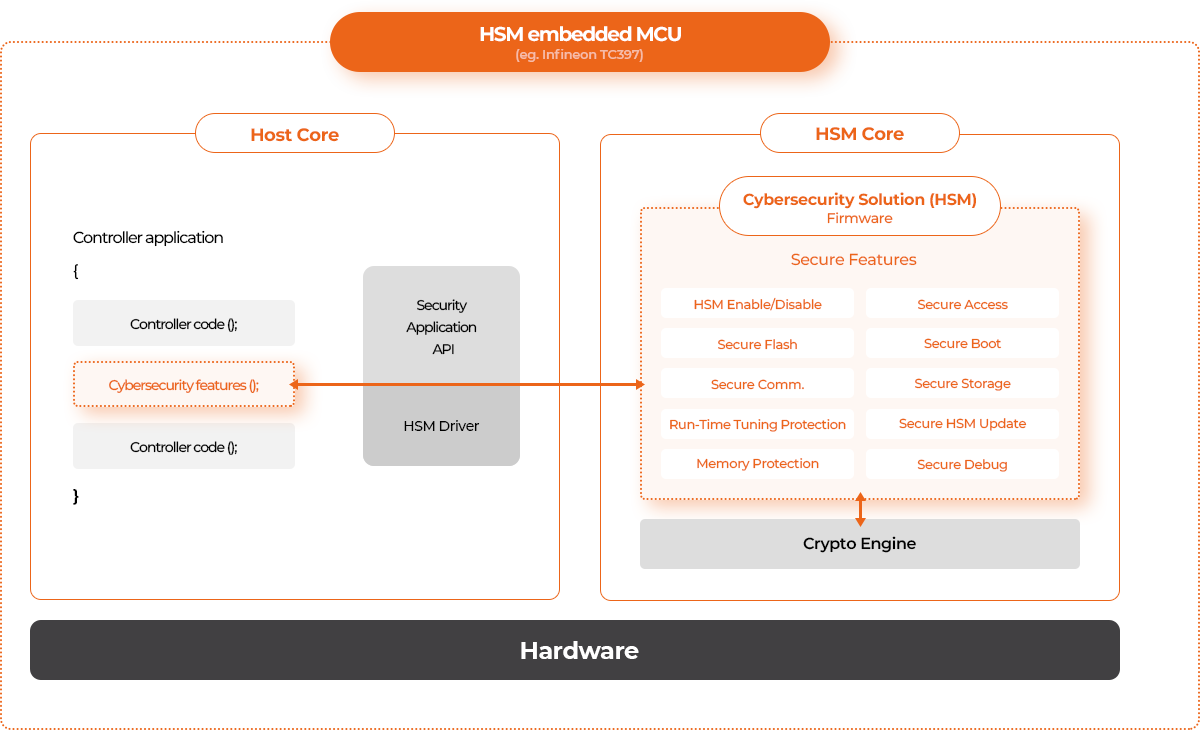
- Cybersecurity application (Secure Access, Secure Boot, Secure Flash, Run-time Tuning Protection, Secure Storage, Secure Unlock, Memory Protection, etc.)
- Offer solution optimized for each chip property & chip environment
-

- Applied to production for ICV/BEV of
a Global Automotive OEM -
- Proven track record of applying to 50+ types of controllers designed for mass production
- Reliability ensured with various references
- Applied to production for ICV/BEV of
and Cybersecurity features.
| Algorithms | Specification | Support | ||
|---|---|---|---|---|
| SW Library | HW Acc (EVITA Medium / Full) |
HW Acc (EVITA Full) |
||
| AES | Supported Key Sizes: 128 / 192 bit | O | O | O |
| Supported Modes: ECB, CBC, CTR, GCM, XTS | ||||
| MAC | AES-CMAC, HMAC-SHA2 | O | O (CMAC Only) |
O (CMAC Only) |
| Random Number Generator | NDRNG: TRNG | O | O | O |
| DRBG: Hash-DRBG, HMAC-DRBG | ||||
| Hash | SHA-256, SHA-512 | O | X | O |
| RSA | Moduli: 1024 / 2048 bit | O | X | X |
| Fast decryption with CRT | ||||
| Key Generation | ||||
| ECDSA | Moduli: 256 bit | O | X | O |
| ECDSA signature generation/verification | ||||
| Diffie-Hellman Key Agreement | dhEphem with KDF | O | X | X |
| PKCS#1 | OAEP / PSS / PKCS#1-V1_5 | O | X | X |
| Certificate | X.509 parser including a DER parser | O | X | X |
| Application | Contents |
|---|---|
| HSM Enable/Disable | Activation / De-Activation of HSM Function |
| Secure Access | Certificate based Seed & Key authentication process |
| Secure Flash | Secure firmware update by certificate based electronic-signature verification |
| Secure Boot | Minimization of boot time by HW-AES based CMAC verification |
| Secure Communication | Verification of communication message integrity through addition of MAC and counter value |
| Secure Storage | Secure storage for cryptographic key, certificate, log, and etc. |
| Run-Time Tuning Protection | Real-time search for any illegal change of operating firmware |
| Secure HSM Update | Secure HSM firmware update |
| Memory Protection | Protection for writing / reading of flash memory |
| Secure Debug | Debugging interface access control |