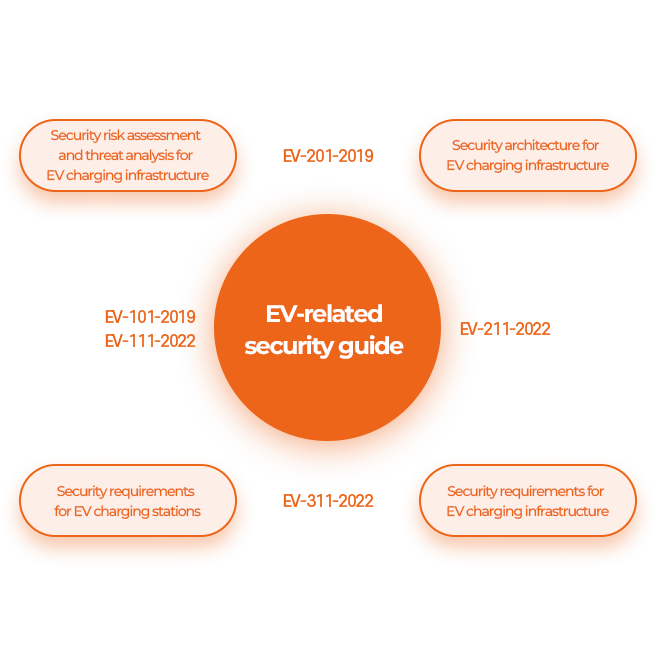
Global charging point operators (CPOs) are increasingly imposing cybersecurity requirements on EV chargers as they become prime targets for cyberattacks.
EV chargers are vulnerable to various threats, including the leakage of sensitive customer information, manipulation of power systems, and potential takeover of vehicle controls.
Moreover, they can be exploited to infiltrate the internal networks of connected vehicles, enabling high-risk attacks with potentially catastrophic consequences.
Ensuring robust cybersecurity is therefore a critical factor in enhancing the global competitiveness of EV chargers.
-
I want to know what security vulnerabilities exist in chargers.
-
I want to conduct various and systematic security tests.
-
I want to prepare for cybersecurity requirements based on charger-related regulations and standards.
-
I need a cybersecurity roadmap with a mid to long-term perspective.
-

- Cybersecurity consulting specialized for chargers
-
- Identifying and analyzing charger systems
- Identifying EV Supply Equipment (EVSE) components
- Conducting Threat Analysis and Risk Assessment (TARA)
- Establishing security measures based on cybersecurity threat priorities
-

- Systematic security testing by a professional Red Team
-
- Setting up the environment and deriving test cases
- Performing vulnerability checks and security tests (simulated hacking/fuzzing tests)
- Possession of specialized security testing equipment (fuzzing tool, reversing equipment, signal analysis equipment, etc.)
- Providing security event analysis results
-

- Providing security measures guide based on the entire roadmap
-
- Measures to mitigate cybersecurity threats (encryption of key data, application of HSM (Hardware Security Module) in control board, strengthening of system access security, etc.)
- Checking the compliance with security requirements
- Deriving short-term and mid- to long-term security measures
- Checking the implementation of security measures