[Series] FESCARO's Automotive Cybersecurity FAQs
FESCARO has been operating the ‘FAQs Series’ to address cybersecurity issues for stakeholders in the automotive industry. We have conducted live webinars on four key topics, and the expert panel from FESCARO provided answers to the most commonly asked questions from industry professionals. If you missed a webinar on a topic that interests you, you can access both the recorded video and a text summary (FAQs) at the following link.
# FAQs Series
1. Cybersecurity Strategies for Tiers (Emerging-OEMs oriented)
2. Comprehensive Guide on Cybersecurity Solutions & Engineering
3. Cybersecurity Testing method based on VTA Success Stories
4. ECU Cybersecurity guidance : From production to post-mass production
5. How Korea’s Motor Vehicle Management Act Amendment impacts OEMs and Tiers

The very first of webinar, <Cybersecurity Strategies 'TALK' (Emerging-OEMs oriented)> launched successfully on February!
The response was amazing! We had about 100 participants from approximately 30 different companies pre-register for the event. We have received questions from Tier companies in advance, and also those during pre-registration. We've covered a total of 7 most common concerns today.
FESCARO's experts with an average of 20 years or more of experience provided clear and insightful advice.
Let's dive in and discover the valuable insights from
• CEO Hong Seok-min, an expert in automotive cybersecurity,
• Director Ku Seong-seo, an automotive software development expert,
• Team leader Choi Kwang-mook, cybersecurity consulting leader specializing in automotive
security certification.
■ QUESTIONS LIST
![]()
■ Video Ver.
■ Text Ver.
1. What cybersecurity do OEMs require from tiers?
The cybersecurity-related requests that both domestic and global
OEMs ask to Tier companies include the following items. (Some items might vary
based on each specific OEM's requirements)
· Item (ECU) level TARA
· Cybersecurity engineering (applied with security solutions,
verified by security testing)
· Organizations and processes related to cybersecurity
· CIA (Cybersecurity Interface Agreement)
In most cases, OEMs carry out
TARA (Threat Analysis and Risk Assessment) at the actual vehicle level and determine cybersecurity goals and requirements for individual items
beforehand. For OEMs that place a strong emphasis on
cybersecurity, there are instances where they ask tiers to conduct TARA at the ECU
level. To meet security requirements,
Tiers need to create various security
applications like Secure Boot and Secure Flash for the ECU.
Additionally, security testing is crucial to ensure that the
OEM's security requirements are effectively met through these applications.
For successful engineering
activities such as cybersecurity development, verification, and operation, Tiers
must establish internal cybersecurity-related teams
and processes that align with business objectives. The prerequisite for this is to engage in R&R discussions
and finalize contracts for cybersecurity tasks between OEM and Tier, known as
the Cybersecurity Interface Agreement (CIA).
However, sometimes OEM requirements can be hard to understand or
vague. In such situations, it's best to interpret them in a way that benefits
the Tier the most while still meeting the basic criteria for OEMs to achieve
UN R155 certification. Therefore, initiating discussions with OEMs about cybersecurity tasks
right at the project's start is crucial. The cybersecurity
manager, often responsible for this, should negotiate
to benefit the Tier while meeting the minimum requirements for OEM
certification. This involves negotiating properly with the
OEM's representative to optimize the reuse of existing materials.
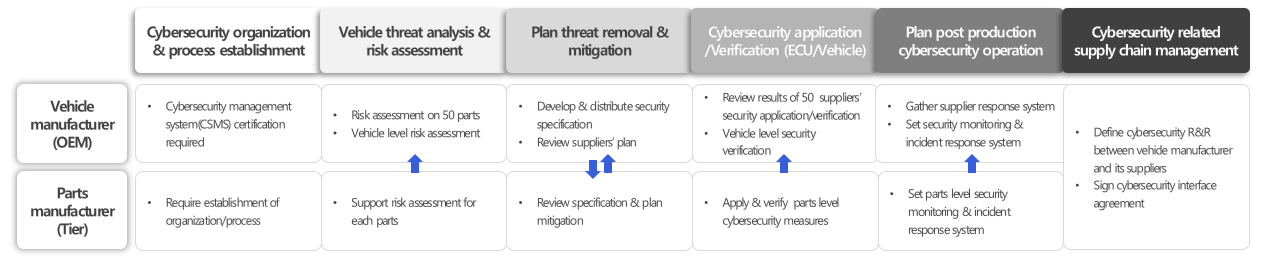
To do a good job as a cybersecurity manager, complete understanding about
the process of acquiring the UN R155 certification for OEM is required. To
summarize, both OEMs and tiers need to establish cybersecurity-related teams
and processes. Moreover, they determine cybersecurity goals and requirements through TARA activities conducted on the vehicle level, system level, and the
ECU level for the specific vehicle type undergoing certification.
To ensure compliance with cybersecurity requirements, OEMs create
and share precise design and validation specifications related to cybersecurity
engineering with Tiers. Since these
specifications are general and intended for multiple OEMs, it's often
challenging to address all the unique aspects of ECUs,
the specific features of new cars, and the individual characteristics of
different tiers. To bridge this gap, OEMs engage in coordination and discussions
with each tier. Using the outcomes of these discussions, they then move forward
with the cybersecurity engineering process, ultimately leading to the Start of
Production (SOP) phase.
Following the SOP, the process undergoes operational stages, including cybersecurity threat monitoring and incident response, until its scrapping(end of support). In terms of the aspects discussed earlier, the CIA plays a crucial role in defining R&R and completing the contract between the OEM and tier. To put it simply, the main approach of CIA is to maximize the reuse of existing components while ensuring the core requirements needed for the OEM's certification.
2. Do OEMs not perform TARA?
Tiers
also require TARA performance. Many people might think that TARA is done only once during the
concept phase. However, TARA is utilized not
only during the conceptual stage but also throughout the development and
post-development phases. This is due to the fact that cybersecurity risks can emerge at
any point during a vehicle's lifecycle.
![]()
When facing a cybersecurity incident, it's crucial to thoroughly
analyze the cybersecurity threat and evaluate the associated risk. TARA
represents a cybersecurity risk management approach. It classifies whether an
immediate response is necessary, whether the task should be addressed promptly,
whether collaboration with others is needed for a delayed response, and the
appropriate level of security measures required. As previously stated, TARA is a continuous
process that must be carried out across the entirety of the
project's life cycle, extending beyond the initial
conceptual stage. Hence, it becomes an essential
aspect that should be ingrained within the
tier's internal operations.
3. Where should I begin with CSMS?
From the tier's point of view, there are two ways to approach CSMS
response. The first involves setting up a cybersecurity management system in
accordance with the ISO/SAE 21434 standard. The second pertains to establishing
a dedicated system for effectively addressing the Cybersecurity Interface
Agreement (CIA) between the OEM and Tier.
The fulfillment of both aspects
can be achieved through the
establishment of a cybersecurity management system that aligns with the ISO/SAE
21434 standard. Setting up an appropriate cybersecurity
management system encompasses the following measures:
· Drafting guidelines for handling the CIA signing process between
OEM and Tier, which encompasses the cybersecurity interface agreement process.
· Establishing a comprehensive cybersecurity management system along
with corresponding rules, including the cybersecurity organization.
· Developing guidelines for conducting cybersecurity Threat Analysis
and Risk Assessment (TARA) activities.
· Defining procedures for integrating and verifying OEM’s
cybersecurity requirements.
· Creating guidelines for the application of cybersecurity
principles within production processes.
· Creating a system that actively monitors cybersecurity-related
information and events, while also conducting analysis and management of
identified vulnerabilities.
· Formulating guidelines for the appropriate response in the event
of a cybersecurity incident.
By implementing this
cybersecurity management system, you will be well-equipped to address a multitude of requirements coming from OEMs in the field
of cybersecurity. Building a cybersecurity management system in accordance with
ISO/SAE 21434 can be challenging, as knowing where to begin and how to proceed
might not be straightforward. In practice, achieving this without expert
guidance, such as professional consulting, can be daunting. Therefore, both
OEMs and many tiers often seek assistance from specialized companies like us to
navigate this complex process effectively. Ultimately, however, it is necessary
to internalize this cybersecurity
management system.
![]()
From a professional consulting perspective, the process of
establishing a cybersecurity management system can be categorized into three
distinct stages. First, the consulting service conducts
a gap analysis aimed at designing and constructing a
cybersecurity management system tailored to the organization's
existing circumstances.
Second, a cybersecurity
internalization project is chosen, and the consulting service guides the
organization through the process of project
implementation in accordance with the established procedures. We assist in planning and setting
up teams for projects related to cybersecurity response, help with the CIA
contract signing process, and provide support for the TARA process. TARA
experts are dispatched when necessary. We also support designing, applying, and
validating security solutions during product development. The red team will be
put in if necessary. Also, we provide help for ensuring security during
production, and assist in monitoring events, and managing vulnerabilities
throughout the entire life cycle of the vehicle.
Thirdly, ISO/SAE 21434 mandates
cybersecurity audits and project assessments,
and we back up this process. Addressing process audits for each project places
a significant burden on development and quality teams. To counter this
challenge, obtaining a dependable CSMS
certification can enhance productivity significantly.
4. I want to reuse the results of previous projects in new projects.
The extent of work for
cybersecurity deliverables is established via the Cybersecurity Interface
Agreement (CIA) established between the OEM and Tier. Every output mentioned in the CIA can be
categorized into either reusing an existing
output or generating a new one.
The decision to reuse these
artifacts should be made after thoroughly examining the
item definition and cybersecurity specifications. When conducting an item definition review, it's important to
pinpoint any alterations in item functionality, security assets, or
modifications to the operating environment. Similarly, during a cybersecurity
specification review, the focus should be on recognizing any shifts in security
requirements or security controls.
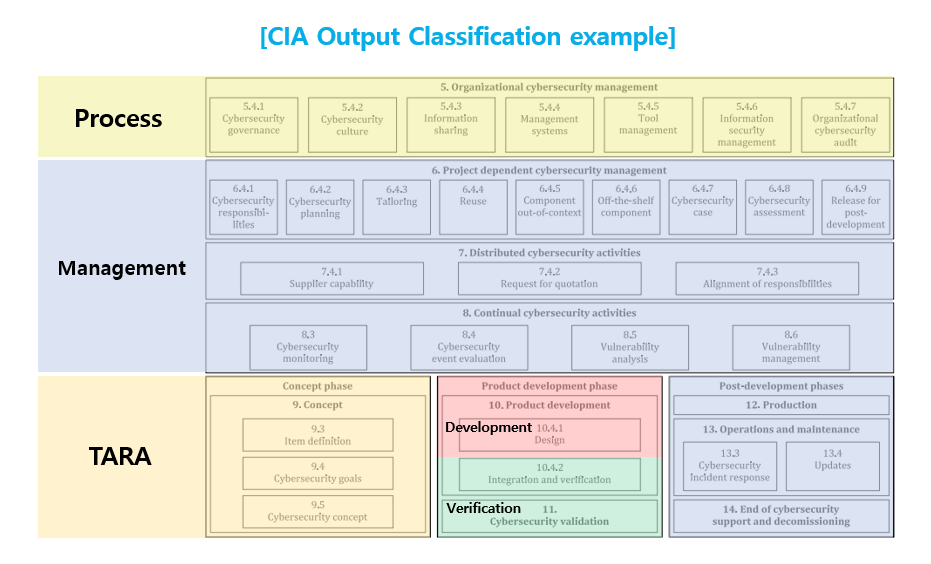
To facilitate the process of output reuse, CIA outputs can be
conveniently organized and categorized as follows. The majority of cybersecurity "process" outputs are
mostly suitable for reuse, whereas "management" outputs demand guided adjustments. "TARA and Verification" outputs can be reused, but it's important to factor in any modifications in
cybersecurity specifications, the operating environment, and related threat
scenarios or vulnerabilities. "Cybersecurity development" outputs are generally reusable, although changes to the cybersecurity specifications
need consideration. In essence, with the exception of chapters
9, 10, and 11, a substantial portion of the outputs can be readily reused.
It's essential to conduct a reuse analysis specifically for the deliverables of
chapters 9, 10, and 11. For example, if it’s decided to add new cybersecurity features,
that means changes to the security functions in the product is necessary. And
not only that, verification testcase also needs to be modified. Here's another
example, even if the product specifications
do not change, if the environment it's used in changes, additional TARA process
is needed. Also, when we bring in an external connection, we have to include
more security measures. And if the vehicle protection model changes, it affects
how we assess security risks. In simple terms, based on the reuse analysis
results, we can decide whether to change specifications or design.
5.
When it comes to cybersecurity vulnerability management, there are two important aspects to consider. First, it's important to handle security vulnerabilities from the development phase to SOP, and throughout the entire life cycle after SOP. Second, we need to take care of vulnerabilities found in different sources.
When it comes to cybersecurity, it's crucial to know that security
breaches can happen even after the SOP (Start Of Production), when the product
development is completed. This is because the development of hacking technology
from hackers are faster than the development of security solutions.
So, whenever there's a security breach or a cybersecurity incident, we have to develop, verify and distribute the security measures, and this has to be repeated throughout the whole life cycle of the vehicle. Normally, when SOP duration is 5 years and the warranty covers 10 years, it will be a total of around 15 years, and in reality, it might even be closer to 20 years. But the current security technology cannot withstand throughout the whole period. That is why it's important to conduct ISO/SAE 21434 Chapter 8 ‘Ongoing cybersecurity activities. Let's see with specific examples.
![]()
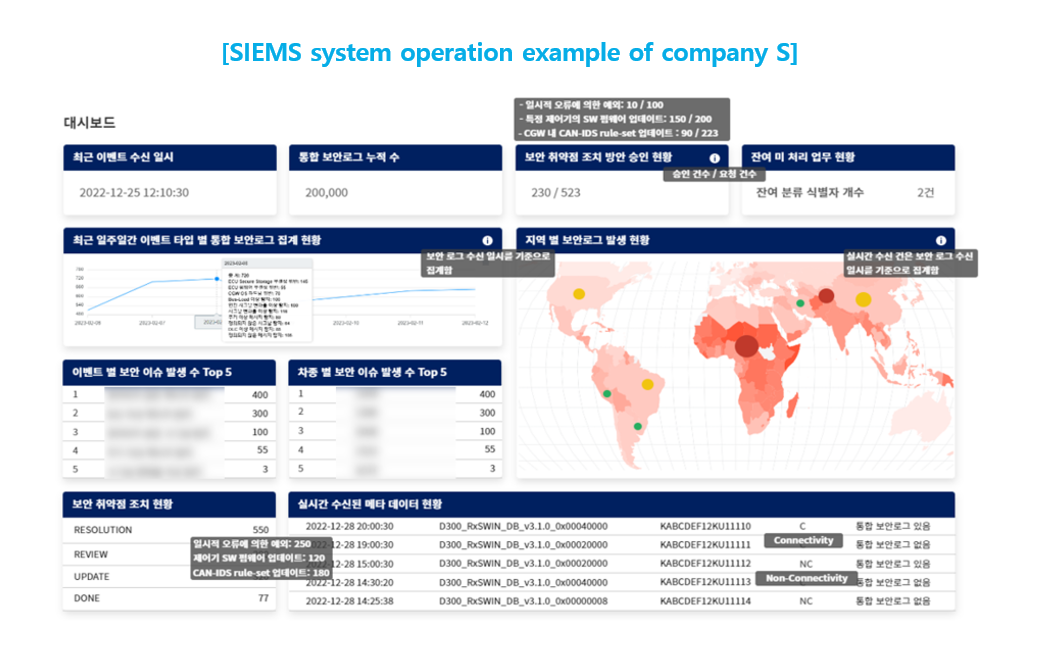
This screen is an example of a vulnerability management ledger.
The sources where vulnerabilities emerge are varied as in the picture.
There can be vulnerabilities from
cybersecurity information and event monitoring, risk list from TARA,
vulnerabilities emerged from project development/verification, security
breaches from the field after SOP. Just like in this example, it's important to
keep a record of vulnerabilities for each project. This is because as mentioned
earlier, the vulnerabilities have to be handled according to the specific
project's traits. And the cybersecurity tasks need to follow the rules in
Chapter 8 of ISO/SAE 21434, which is the 'Guidelines for Ongoing Cybersecurity Activities’.
[ ISO/SAE 21434 Chapter 8 'Guidelines for Ongoing Cybersecurity Activities' ]
· Implement/record of cybersecurity information and event monitoring
· Evaluate whether an identified event is a security weakness
· Check through TARA if the weakness could be a vulnerability in the
project
· Vulnerability management throughout the product life cycle
To internalize the management of cybersecurity vulnerabilities, it is a best practice to build and operate SIEMS (Security Information and Event Management System) system. With this system, it is possible to manage the entire cybersecurity issues and the current situation comprehensively.
6. Every meeting with OEMs leads to more follow-up work due to a lack of cybersecurity knowledge.
We often come across this question when
we communicate with ECU manufacturers, and it's a
challenge we've faced a lot. We've covered a similar kind of
response strategy earlier, and to handle the different requests from OEMs
effectively, it's crucial to have standardized and strategic
response processes.
· Tailoring security requirements
according to product characteristics
· Minimizing modifications due to
changes in OEM's needs by creating outputs following international standards
In general, OEMs have
certain standard requirements for cybersecurity features. However, these
requirements are usually a superset. Since the features of
each ECUs are different, it is hard to apply in entirely. It's
important to really understand what OEMs are requesting and identify what is capable of what is not. If there are things not possible to do, showing different options or explaining why it's not possible is required. And if it's needed,
suggesting plans for what to do next is necessary.
OEMs will take the information provided by these ECU manufacturers to get the type certification. When we look at it from the perspective of the CIA (Cybersecurity Interface Agreement), it's tough for the ECU manufacturers to respond since each OEM's product requirements are different. To work around these challenges, It must be written based on the ISO/SAE 21434 standard and sufficiently explained that it satisfies the international standards to minimize repetition or modification of work.
But the real challenge is that a lot of ECU manufacturers don't
have a dedicated cybersecurity team, which makes it tough to handle the tasks.
The more you discuss with OEMs, the more confusion tends to arise,
making the workload even heavier. To tackle these issues, having experts with
specialized security skills would be a great help. Companies like FESCARO could be
an alternative.
FESCARO currently offers CSMS consulting,
security solutions, and security testing services for local OEMs. We are well-versed in what ECU manufacturers have to
do in order for OEMs to achieve the UN R155 certification, and have a track record
of assisting multiple ECU manufacturers with CSMS consulting, cybersecurity
manager responses, security solutions, and engineering services. We
are here
to provide a clear guide for you to navigate these tasks effectively.
7. Are cybersecurity certifications required for tiers?
In simple terms, no. To clarify, the certification is only required for car manufacturers. UN R155 states that CSMS certification must be obtained by car manufacturers. However in CSMS, it is required to manage the cybersecurity activities of the ECU manufacturers as well.
The detailed process for this is
explained in Chapter 7, 'Distributed Cybersecurity Activities,' of ISO/SAE
21434. The OEM verifies if the ECU manufacturer has established CSMS by using the CIA (Cybersecurity
Interface Agreement). Even though the ECU manufacturers don't directly
have to get
certified, it's required to create
CSMS as per the OEM's requirements. Certain ECU manufacturers might even
earn CSMS certification through a certification body like TS (Technical Service) and get the ISO/SAE 21434
certification.
This certification offers the
reassurance that the company is well-prepared for cybersecurity, giving you an advantage when pursuing
different projects or new projects with OEMs. Certification
bodies currently lack formal certification qualifications or auditor
qualifications. Because of this, organizations like TS are taking on the role
of UN R155 certifications and carrying out ISO/SAE 21434 certifications for tiers.
FESCARO is working in collaboration
with several TS companies, and there have been instances where ECU manufacturers that we have consulted achieved ISO/SAE
21434 certification. Drawing from this collaborative partnership and the
experience gained,
FESCARO is dedicated to providing comprehensive support to ECU manufacturers, ensuring
them to successfully
attain certification.
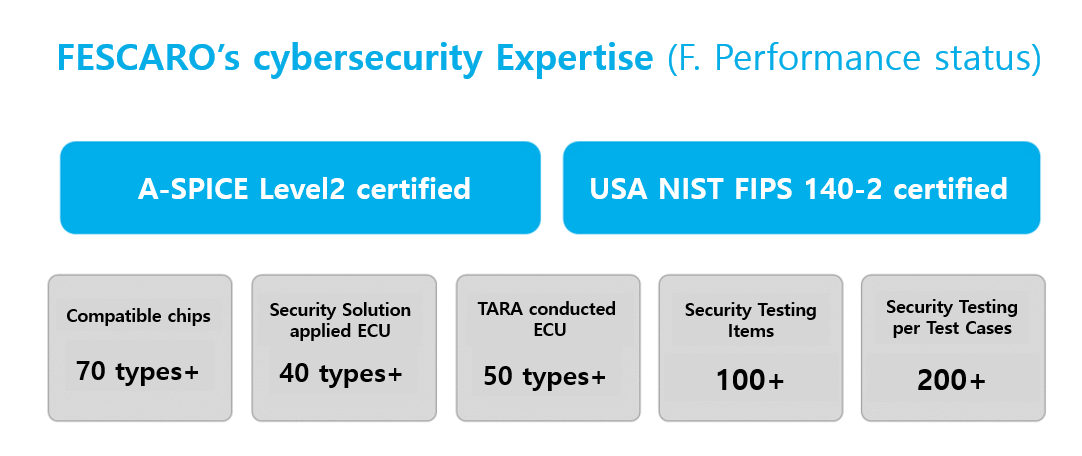
FESCARO has secured CSMS certification from OEMs and ISO/SAE 21434
certification from Tiers.
Our expertise encompasses cybersecurity consulting and engineering
services for a wide range of ECU used in both internal combustion engine vehicles and electric vehicles.
-
PREV No previous post.
-
NEXT [FAQs] Comprehensive Guide on Cybersecurity Solutions & Engineering