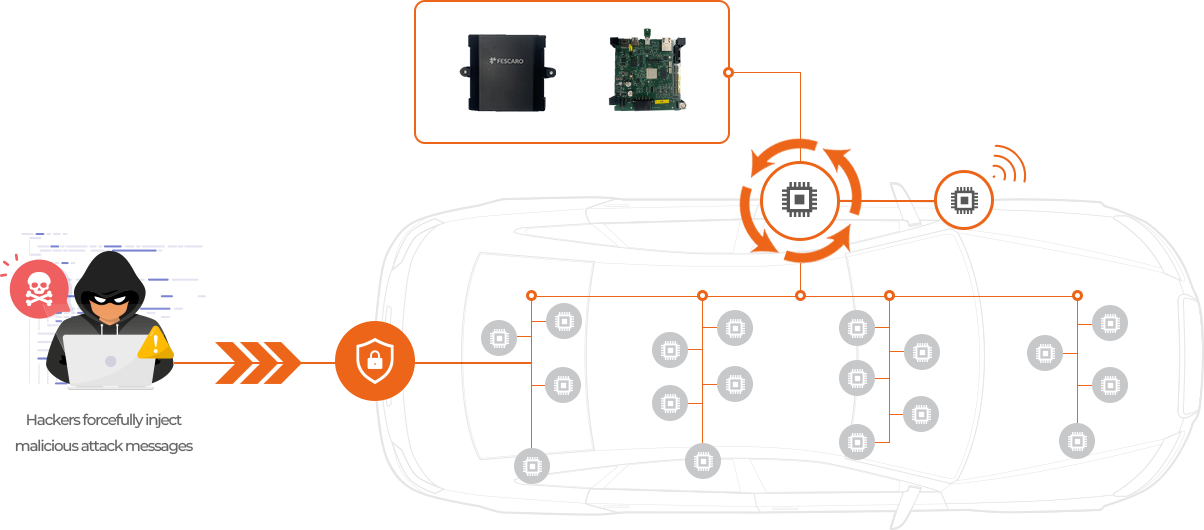
UN R155 states that vehicle manufacturer shall detect and respond appropriately to cybersecurity attacks occurring on vehicles,
and UN R156 states that vehicle manufacturers shall have SW update management system and processes for vehicles and controllers.
To meet these regulations, communication between all controllers connected to the vehicle network must be protected and
the software configuration of the controllers must be managed.
protect communication between controllers?
-
I don't know how to respond to in-vehicle network attacks via external contact points such as OBD-II or controller SW modification (e.g., arbitrary manipulation, DoS, etc.).
-
I don't know how to manage the software updates and configurations of controllers that needs to respond to various quality issues, cybersecurity incidents, and performance improvements.
-

- Extension considered, AutoSAR based platform
-
- Up-to-date chipset with high performance
(AP : Cortex-A53 core - 1.0 GHz, MCU : 3x Cortex-M7
cores - 400 MHz), 1GB DDR, 8G EMMC, 8M NOR Flash memory) - AUTOSAR 4.3 applied
- AP(Linux based) + MCU(RTOS based) architecture ensures easy extension
(Ethernet, OTA, Digital Key, etc.) - Support basic features of the Central Gateway perfectly
(CAN Routing, Network Management, Diagnostics, etc.)
- Up-to-date chipset with high performance
-

- Latest Cybersecurity solution embedded
-
- Intrusion Detection Technology is applied to IVN (CAN-IDS)
- Forensic Technology is applied for Automotive Cybersecurity
- HSM with EVITA Full
- Latest cybersecurity applications applied (Secure Boot, Secure Storage,
Runtime Tuning Protection, Secure Debug, Memory Protection) - Diagnostic cybersecurity features (Secure Unlock, Secure Access, Secure Flash)
-

- SW update management in compliance with regulatory regulations
-
- RxSWIN system management
- Configuration management for SW/HW of entire controllers of the vehicle
- Controller SW Update management
- Technologies and platforms scalable to OTA
and check SW Update Management of entire controllers.