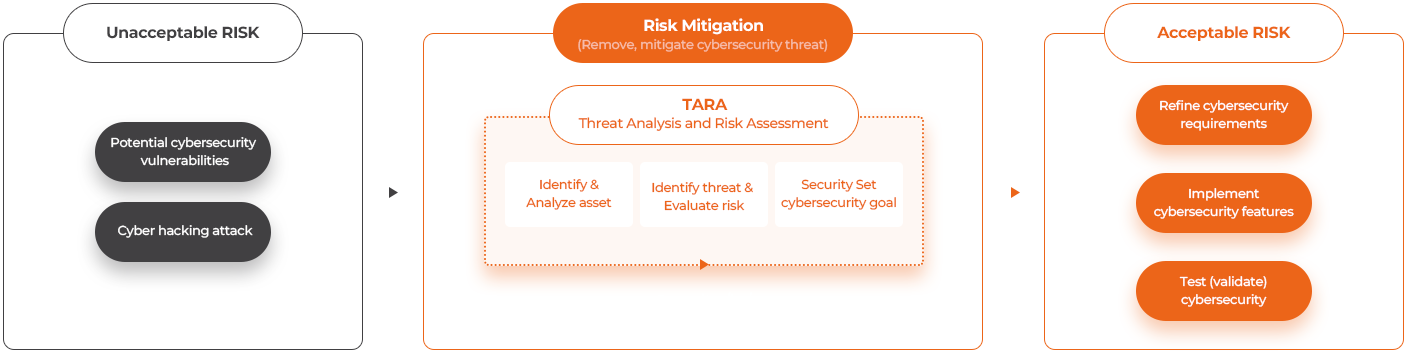
OEM would like to perform TARA(Threat Analysis and Risk Assessment) to identify cybersecurity threat that may affect vehicle/controller
and to evaluate the potential risk that may arise from that threat. Accurate TARA result can only be derived when cybersecurity professionals are available.
How should we handle TARA required by OEMs?
-
I don’t know why TARA should be performed, and how to do TARA.
-
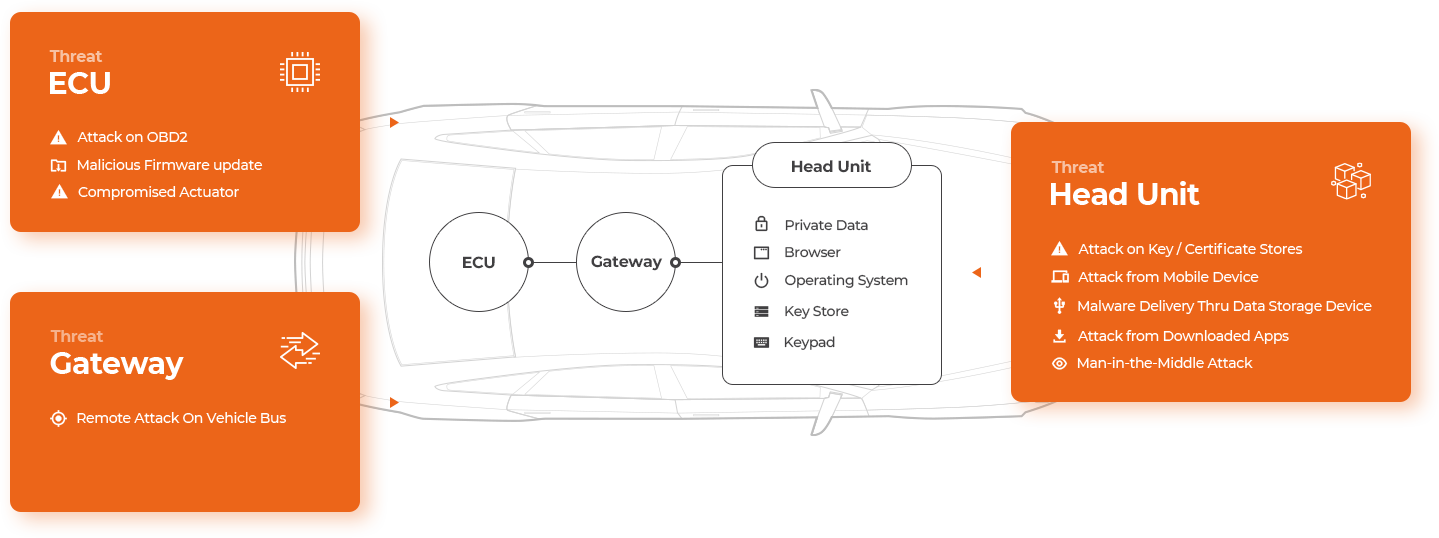
Asset identification, threat scenario identification, impact rating, attack path analysis, etc. are required in TARA, but I don’t understand what it means.
-
There are vast number of projects that requires TARA, but we lack experts.
-
I don’t know whether we are doing TARA in the right way.
Identify potential vulnerabilities for ICVs to EVs.
-

- Group of TARA Engineering Experts
-
- Group with cybersecurity professional competency
- Group with controller development & production experience
- Collaboration & Harmonization between the two group
-

- Analyzed entire controllers of
a Global Automotive OEM ICV & BEV -
- Performed Vehicle level TARA
- Performed TARA for 50+ Controllers
- Identify controller property & its potential threats
- Identify vulnerabilities according to the risk level for each controller
- Analyzed entire controllers of
-

- Engineering system satisfies International Standard
-
- Offer ISO/SAE 21434 based manual & work product(WP-09-xx, WP-15-xx)
- Use its own development tool for work efficiency
- Derive effective and accurate result integrating international standard & know-how
Check out potential Cybersecurity threats using TARA.